SSL security technology protects most websites that deal with critical security data. SSL establishes a secure, encrypted link between a server and a client. Most commonly, the connection is between a web server and a browser or email client on a client computer. SSL is commonly referred to as a security protocol, because it specifies algorithms for encryption and necessary variables for connection encryption. The purpose of securing a
connection with SSL is to protect data, such as credit card numbers, logon credentials, and other critical data, while the data transfers between a client and a server.
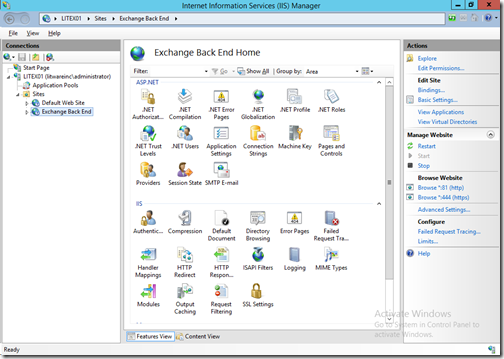
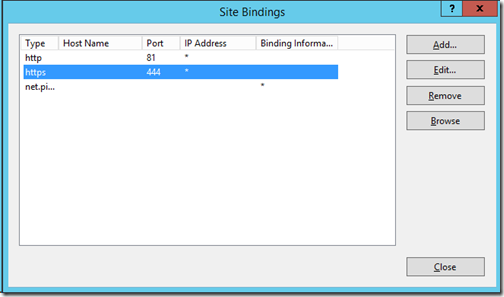
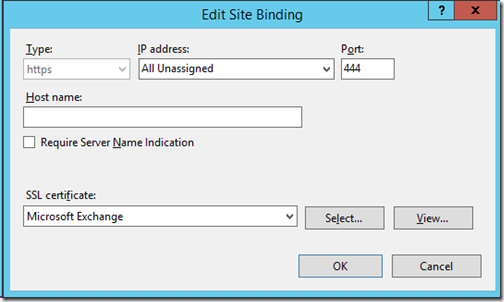
To establish a connection protected by SSL, you must install the certificate on the server. Your internal CA or a public CA can issue a certificate for SSL. For websites available on the Internet, it is common to have a certificate issued by a public CA because of the trust issues. Howev er, you can also use a certificate issued by your local CA. A connection can be secured with both types of certificates, but most clients that connect to the website where the certificate is installed cannot trust an internally issued certificate. The fact that the certificate is untrusted will not prevent it from securing a connection, but it will present clients with a warning message when they connect to your website. Most companies want to avoid this, so the most secure websites on the Internet use public certificates. Internet browsers come with a preinstalled list of trusted CAs, and they store this list in the trusted root CA store.
Note: Buying a public SSL certificate does not automatically guarantee that all clients will trust the certificate. Make sure that you choose a certificate vendor that is trusted globally and
has its CA certificates present in the client’s preinstalled trusted root CA store.
Securing a Connection with an SSL Certificate
Each certificate has a key pair associated with it after it is issued. The key pair consists of a public key and a private key. These keys work together in an encryption process. Data that is encrypted with a public key can be decrypted only with a corresponding private key, and vice versa. Each key pair is unique. Besides having a key pair, each certificate also has its subject name that specifies the identity of the server or website where the certificate is installed.
When a web browser connects to a secure website, the client and server establish an SSL connection. The SSL connection establishes during the SSL handshake. This handshake process occurs through the
following steps:
1. The user types or clicks an HTTPs URL in a web browser.
2. The web browser software connects to a website and requests for the server to identify itself.
3. The web server sends its SSL certificate. With the certificate, the server also distributes its public key to the client.
4. The client performs a check of the server certificate. It checks the subject name and compares it with the URL that it used to access the server. It also checks if any of the CAs in the trusted root CA store issue the certificate and it checks the certificate revocation list distribution point (CDP) locations to verify if the certificate is revoked.
5. If all checks pass, the client generates a symmetric encryption key. The client and server use a symmetric key for decrypting data because the public and private key pairs are not very efficient in
encrypting and decrypting large amounts of data. The client generates a symmetric key and then encrypts this key with the server’s public key. After that, the client sends the encrypted symmetric key to the server.
6. The server uses its private key to decrypt the encrypted symmetric key. Now both the server and the client have a symmetric key, and the secure data transfer can begin.
This process involves several very important checks. First, the server proves its identity to the client by presenting its SSL certificate. If the server name in the certificate matches the URL that the client requested, and if a trusted CA issues the certificate, the client trusts that the server has valid identity. The client has also checked the validity of the certificate by checking its lifetime and CDP location for the certificate revocation lists (CRLs). This means that establishing an SSL session does more than manage
encryption; it also provides authentication from a server to a client.
Note: Client authentication is not part of the classic SSL handshake. This means that a client does not have to provide its identity to the server. However, you also can configure your website to require client authentication. The client also can use a certificate to authenticate itself.
Note: A certificate can be issued only for a server name or alias, not for a full URL. For example, a certificate with the common name www.adatum.com will also protect URL www.adatum.com/sales or similar.
Source :- MOC-20412